Managed ATTACK
Breach & Attack Simulation
Inceptus’ Managed ATTACK runs continuous, on demand cybersecurity simulations at any time without affecting organization’s systems. As a fully managed breach and attack platform, it simulates multi-vector, internal or external attacks by targeting the latest vulnerabilities, including those that are in the wild. These simulated attacks expose vulnerability gaps which allows the organization to determine if its security architecture provides the right protection and if its configurations are properly implemented.
Breach and attack simulations have made it faster, simpler and less expensive to get enterprise-grade visibility into the effectiveness of current security controls and improves an organization’s security posture.

Managed ATTACK Facts
Why Penetration Testing is Inefficient

Penetration Testing vs. Breach and Attack Simulations

Areas Tested
Value Proposition
Value Proposition
.
Value Proposition
Value Proposition
Value Proposition

Breach and Attack Simulation Made Simple
Inceptus provides an advanced technology platform that can launch automated simulations of cyber-attacks against your organization, immediately exposing security gaps and providing mitigation guidelines to close each one
24x7 Visibility of Security Gaps
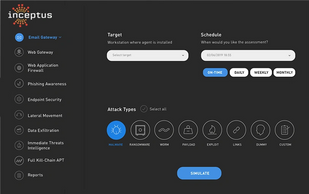
Simulated Attacks
Evaluate Controls to Identify Gaps
Evaluate Controls to Identify Gaps
Inceptus tests the strength of your security by simulating real cyber attacks across all attack vectors based on MITRE ATTACK™. We protect your organization from threats before they ever show up.
Evaluate Controls to Identify Gaps
Evaluate Controls to Identify Gaps
Evaluate Controls to Identify Gaps
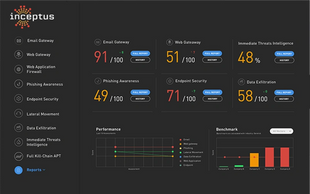
Managed ATTACK provides Risk Scores and a clear report that details your up-to-the-moment security posture. Inceptus uses proven methodologies to evaluate cyber risk such as NIST, CVSS V3, and Microsoft DREAD.
Remediate with Actionable Insights
Evaluate Controls to Identify Gaps
Remediate with Actionable Insights
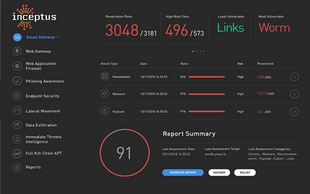
Inceptus stays one step of the attackers by providing direct instructions to reduce your organization’s attach surface and easily prioritizes which gaps need to be addressed first.
Cookie Policy
This website uses cookies. By continuing to use this site, you accept our use of cookies.